Reversing Hero
Level 1
Introduction
So today I decided to write a small writeup on Level 1 of ReversingHero Challenge. This is a pretty easy Level as it is the first. But the difficulty will increase advancing further Levels. While learning RE in my 3rd year of college, I came across a thread on reddit which was addressed to RE newbies to give some learning Resources. I then found out about ReversingHero challenge there. It is a perfect challenge for RE Newbies.
I have used Remnux VM in this writeup which you can download from here. You can use any Linux Distro to solve this challenge but I wanted to learn Remnux thus I will be pasting the output from it. You can download the binary file from reversinghero.com. You will be greeted with an intriguing content. All Credits to xorpd for creating this challenge and giving me a permission to post a writeup. You can visit his Personal Website here.
Diving In
So after Downloading I ran the file command to find out that the file was a Linux Executable(ELF) File.
remnux@remnux:~/Downloads$ file reversinghero
reversinghero: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked (uses shared libs), not stripped
So the ELF File is not stripped.
We now Execute the file.
remnux@remnux:~/Downloads$ ./reversinghero
@ 1/p1
@ 1/x1
] +
After Executing the binary we get the above output. After running ls command we find that 2 new files p1 and x1 have been extracted in a new folder “1”.
remnux@remnux:~/Downloads$ ls
1 reversinghero
remnux@remnux:~/Downloads$ cd 1
remnux@remnux:~/Downloads/1$ ls
p1 x1
remnux@remnux:~/Downloads/1$ file *
p1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked (uses shared libs), not stripped
x1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked (uses shared libs), not stripped
remnux@remnux:~/Downloads/1$ ls -al
total 572
drwx------ 2 remnux remnux 4096 Sep 18 10:01 .
drwx------ 3 remnux remnux 4096 Sep 18 10:01 ..
-rw-rw-r-- 1 remnux remnux 566160 Sep 18 10:01 p1
-rw-rw-r-- 1 remnux remnux 6640 Sep 18 10:01 x1
Here we see both the extracted files are ELF. We make both the files executable by running chmod command.
remnux@remnux:~/Downloads/1$ chmod +x x1
remnux@remnux:~/Downloads/1$ ls
remnux@remnux:~/Downloads/1$ chmod +x p1
remnux@remnux:~/Downloads/1$ ./x1
Then we try to execute p1.
remnux@remnux:~/Downloads/1$ ./p1
> password
] -
Here I entered password but it needs a different input. We will try to execute x1.
remnux@remnux:~/Downloads/1$ ./x1
? lsdjfsjdofijwselvsd
! -
Here I entered a random string to show that the ELF needs some kind of password. So first advice I have got from other RE Specialists is to check all the strings contained in the executable file. See if there is any useful word you find like a password, temporary file, config file keyword, location etc.
remnux@remnux:~/Downloads/1$ strings x1
/lib64/ld-linux-x86-64.so.2
libc.so.6
printf
fdopen
fclose
memset
strcmp
strlen
exit
fgets
strcspn
GLIBC_2.2.5
ATAUAVI
A^A]A\
&EI1
ATAUAUI
A]A]A\
ATAUAUH
A]A]A\
d(-_-)b//d(+_+)b\\d(-_-)b
! +
ReversingHero
#<}]
www.xorpd.net
%02X
_DYNAMIC
_GLOBAL_OFFSET_TABLE_
_edata
fclose@@GLIBC_2.2.5
strlen@@GLIBC_2.2.5
printf@@GLIBC_2.2.5
memset@@GLIBC_2.2.5
strcspn@@GLIBC_2.2.5
fgets@@GLIBC_2.2.5
strcmp@@GLIBC_2.2.5
_end
fdopen@@GLIBC_2.2.5
__bss_start
exit@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.plt
.text
.eh_frame
.dynamic
.got.plt
.data
.bss
So here we see few strings in x1 executable.
Most eyecatching was (-_-)b//d(+_+)b\\d(-_-)b
We now just copy and paste this in out input of x1 file.
remnux@remnux:~/Downloads/1$ ./x1
? d(-_-)b//d(+_+)b\\d(-_-)b
! + 3E437BBA43971D612049DE8AD54FDEF068931E8C6D26F63D83742F932E740B6D
Yay!! We got a Flag. Copy this flag and paste as an input to p2.
> 3E437BBA43971D612049DE8AD54FDEF068931E8C6D26F63D83742F932E740B6D
@ 2/p2
@ 2/x2
] +
See it gave a different output than before. It has created a new directory “2”. In the directory there are 2 files, and they are p2 and x2. These are the files for Level 2. I will be writing Level 2 and posting it soon.
Though we have solved this level by just running strings and guessing the password from it, I would advice you to go through the disassembly I have attached below. The screenshots are from Binary Ninja Cloud which is completely free and you can use it to decompile it through their BNIL Decompiler. I would highly recommend you all to use Binary Ninja as it is an emerging software, cheaper than IDA Pro and provides good options to users. I am trying to save up and buy the commercial License from it. They are offering 75% Discount to full time students.
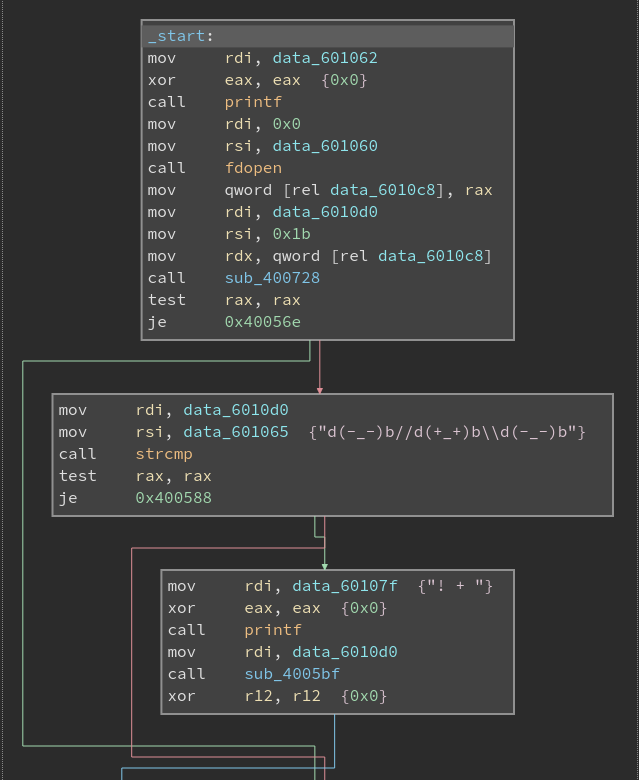
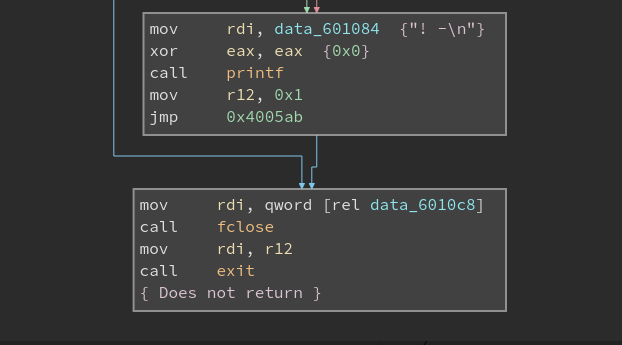
Hint: Check which string is copied to rsi and rdi. And How the result of “! + " or “! -\n” gets printed.