Level 2
Hi World, how are you doing today??
So this is going to be the Level 2 of the ReversingHero Writeup. Once again thanks to xorpd for creating
such wonderful executable and giving me permission to write about it.
Lets jump right into it.
As you saw in previous post, we get a new folder named “2” after completing level_1.
Here we see the same configuration one p and one x file. We make them executable first and also check the
details.
remnux@remnux:~/Downloads/1/2$ ls
p2 x2
remnux@remnux:~/Downloads/1/2$ chmod +x *
remnux@remnux:~/Downloads/1/2$ ls
p2 x2
remnux@remnux:~/Downloads/1/2$ ls -al
total 540
drwx------ 2 remnux remnux 4096 Sep 18 16:09 .
drwx------ 3 remnux remnux 4096 Sep 18 16:09 ..
-rwxrwxr-x 1 remnux remnux 536240 Sep 18 16:09 p2
-rwxrwxr-x 1 remnux remnux 6648 Sep 18 16:09 x2
Let’s run both the files and give them some garbage argument just to see the functionality.
remnux@remnux:~/Downloads/1/2$ ./p2
> lkdkjvlsjdvoslsjdvosjdovjsv
] -
remnux@remnux:~/Downloads/1/2$ ./x2
? lsdjowwejvlsxsvojsojdflsjdviojiovjldjv
! -
So this is same as the first Level. Lets check the strings in the ELF.
remnux@remnux:~/Downloads/1/2$ strings x2
/lib64/ld-linux-x86-64.so.2
libc.so.6
printf
fdopen
fclose
memset
memcmp
strlen
exit
fgets
strcspn
GLIBC_2.2.5
ATAUAVI
A^A]A\
ATAUAVI
A^A]A\
&EI1
ATAUAUI
A]A]A\
ATAUAUH
A]A]A\
89349536319392163324855876422573
! +
ReversingHero
#<}]
www.xorpd.net
%02X
_DYNAMIC
_GLOBAL_OFFSET_TABLE_
_edata
fclose@@GLIBC_2.2.5
strlen@@GLIBC_2.2.5
printf@@GLIBC_2.2.5
memset@@GLIBC_2.2.5
strcspn@@GLIBC_2.2.5
memcmp@@GLIBC_2.2.5
fgets@@GLIBC_2.2.5
_end
fdopen@@GLIBC_2.2.5
__bss_start
exit@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.plt
.text
.eh_frame
.dynamic
.got.plt
.data
.bss
The string that stands out is well 89349536319392163324855876422573 . Lets try to input it in
x1 executable file.
remnux@remnux:~/Downloads/1/2$ ./x2
? 89349536319392163324855876422573
! -
LoL… Doesnt work everytime.
Lets open the file in Binary Ninja Cloud.
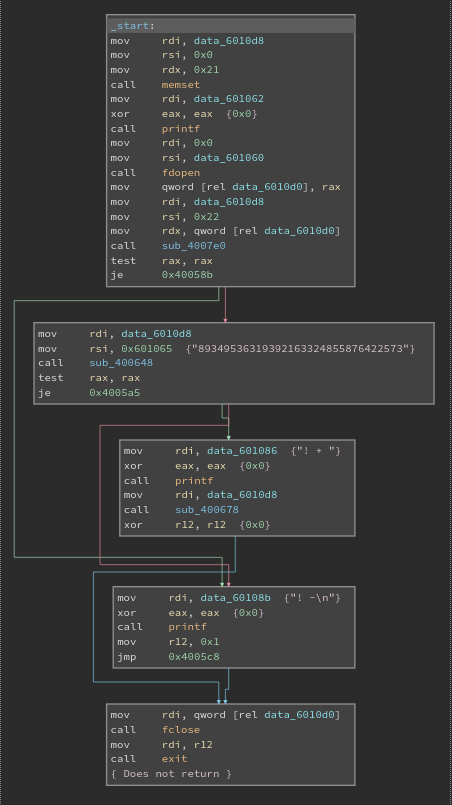
Now we know if we enter any wrong string the executable gives output as ! -(See above when we tried the guessed string). So we definitely
don’t want to go in the 4th box as it gives the same output. What we need is the 3rd box which would give ! + and append a flag then.
Now we try to break down main in x2 executable as simple as possible.
mov rdi, data_6010d8
mov rdx, qword [rel data_6010d0]